Review of created secrets
Once AzureKeyVault is applied, following kubernetes secrets are expected to be created in respective namespace(s).
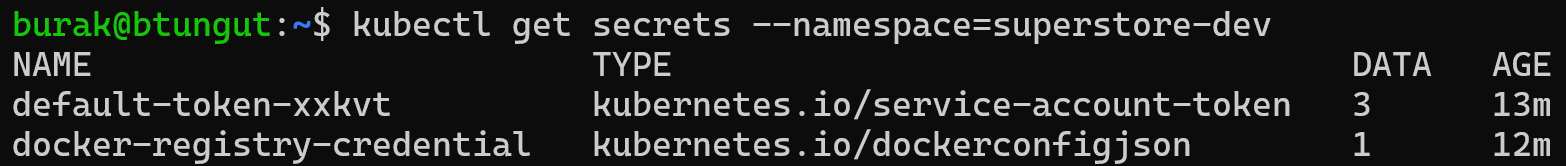
Only docker-registry-credential secret was created due to 3rd managed secret definition.
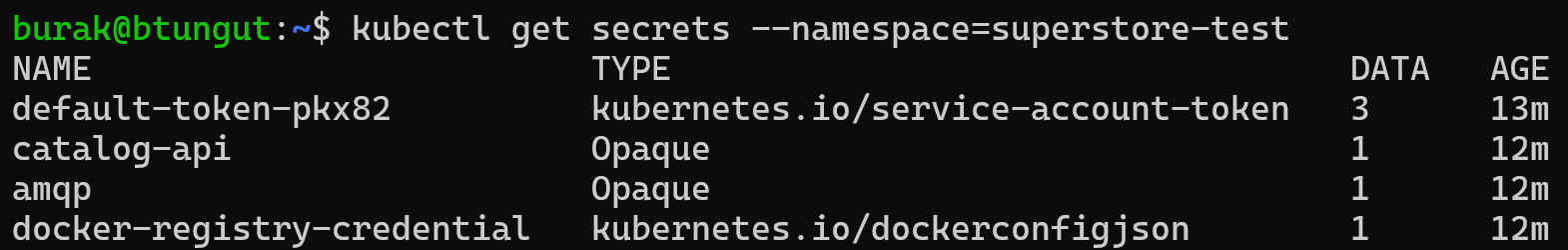
All managed secret definitions are matched with superstore-test namespace. Therefore this namespace includes all three secrets.
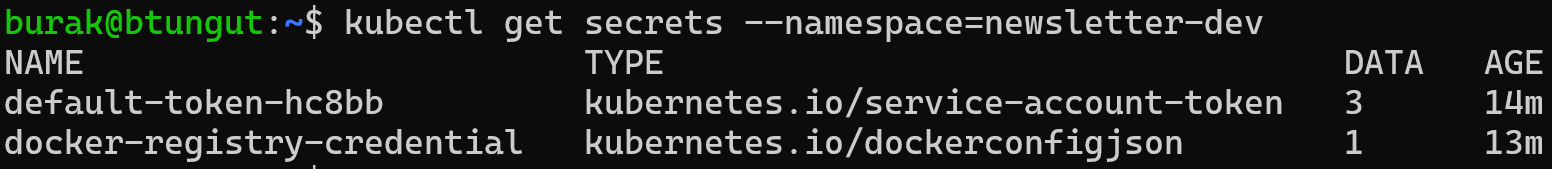
Only docker-registry-credential secret was created due to 3rd managed secret definition.
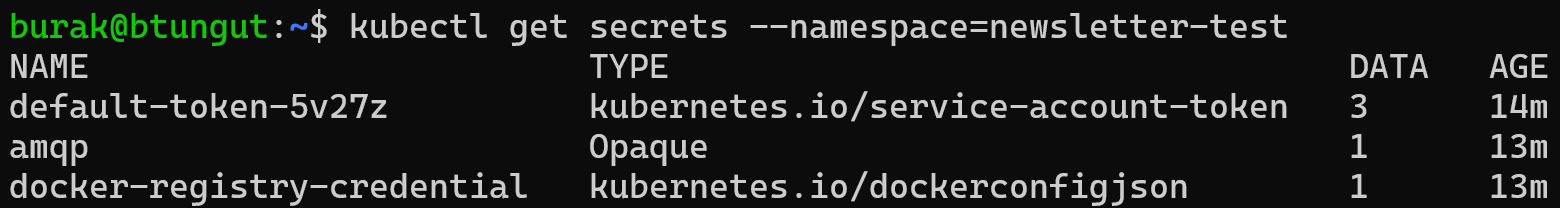
2nd and 3rd definition is matched with newsletter-test namespace.
Before & After of jsonpath declaration
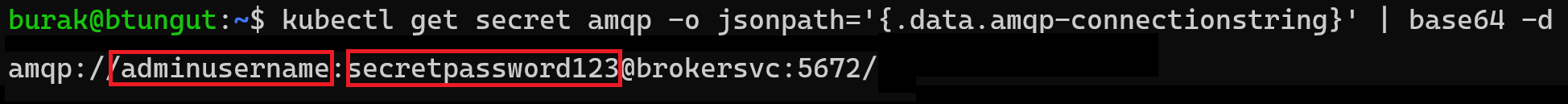
Let’s remember how amqp was declared in .spec.managedSecrets[] and how it is crated as kubernetes cluster;
...
- name: amqp
namespaces:
- "(.+)-test"
type: Opaque
data:
amqp-connectionstring: "amqp://\$['amqp-username']:\$['amqp-password']@brokersvc:5672/"
...
In yaml definition, because of the bash syntax, we have to use \ character to escape $ sign.
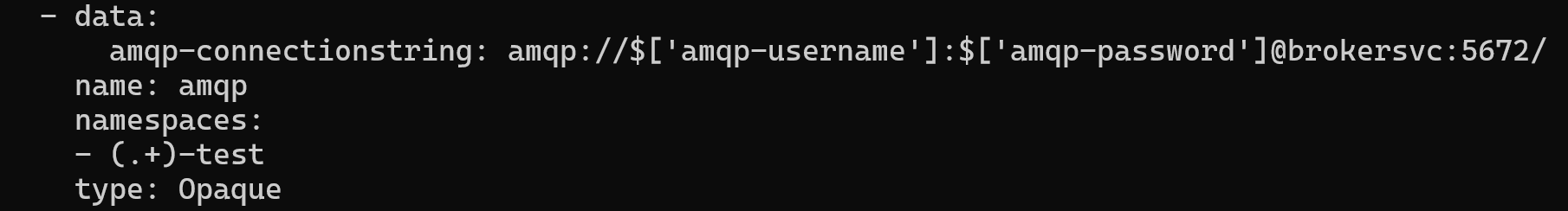
This is how created kubernetes secret looks like;